
Are You Really Who You Say You Are?
24 November, 2021, by Simon Young
Identity proofing is something we participate in pretty much every day of our lives, whether we realise it or not. Any time we are asked to verify our identity, from the innocuous logging into your email or collecting the keys to your hotel room to something that contains more risk to an individual or organisation, such as opening a bank account, we participate in the verification of our identity. Some of these proofing processes may be much more involved than others but the fundamental premise remains the same: a method to verify and authenticate the identity of an individual.
What is an Identity?
An identity can be viewed as a combination of characteristics or attributes which belong to an individual. In turn, we can assert that an individual declares themselves to be somebody - the "claimed identity". By cross-checking information supplied to prove the authenticity of the "claimed identity", the individual can be verified as the "actual identity" or not.
Why is Proofing Important?
Identity Proofing is useful in establishing the validity of an individual's identity. The main driver for Identity Proofing is to reduce the occurrences of some types of fraud. Ensuring the claimed identity is the real identity can help prevent the following:
- obtaining access to services to which they are not entitled
- obtaining access to benefits to which they are not entitled
- obtaining/stealing other personal/financial etc information
- carrying out processes without authorisation from the real identity
The Cost of Identity Fraud
2020 may be viewed as a "perfect storm" for cybercriminals who specialise in identity theft. With a large number of people suddenly finding themselves at home, online activity shot up. Cybercriminals were quick to spot the opportunity with the changing habits and lifestyles by tailoring scams to capitalise on:
In 2020, it is estimated that £738.8 million was lost to unauthorised financial fraud across payment cards, remote banking and cheques in the UK. If you add authorised push payments, that number jumps to £1.26 billion. However, it was not all doom and gloom, another £938 million in card fraud was stopped in 2020.
How Should Identity Proofing Work?
Both the UK Government and the US National Institute of Standards and Technology (NIST) have similar views on how the identity proofing process should work.
The UK Government recommends the following five steps:
1. Gather evidence of the claimed identity.
2. Validate that the evidence is genuine or not.
3. Validate the claimed identity has existed over time.
4. Check if the claimed identity is at high risk of identity fraud.
5. Check the claimed identity belongs to the person claiming it.
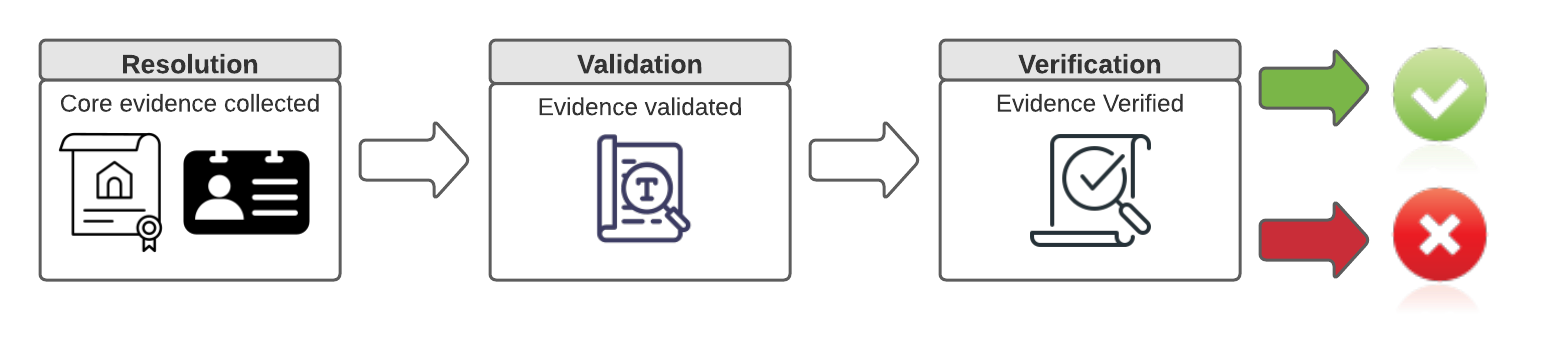
The NIST guidelines present a similar flow:
1. Resolution: Gather core attributes and evidence.
2. Validation: Validate the evidence gathered is authentic, valid and accurate.
3. Verification: Verify the evidence.
When/Where to Identity Proof
As with most things, there is a balance to be struck. Making individuals go through a rigorous identity proofing process when registering for your service can introduce unnecessary friction if you are providing relatively "simple" services, like email, quotations for insurance or online shopping. Generally, the more financial or reputational risk involved in a service, the more thorough the identity proofing should be.
Certainly, you want the assurance that your bank, doctor, employer, telecoms provider, insurance providers and government are performing stronger identity proofing techniques.
Reducing Identity Proofing Barriers
Another friction factor can be the time taken to perform this process. For the most part, all supplied documentation will be reviewed manually but this is hard to scale.
The shift or augmentation to more automated approaches to identity proofing is becoming more desirable. There are several options in this space, ranging from services which will verify documentation of various guises to verification of photo IDs or facial biometrics.
New Threats
With technology advances making it easier to determine risk levels and proof identities, the sophistication of identity theft is also advancing.
With more and more data being stored, the number of data breaches increasing combined with the rising capabilities of AI and deep-fakes, it is harder to rely on more modern automated techniques of verification. "Proof of life" videos which have become more prevalent during the pandemic are more easily circumvented using these emerging technologies.
Closing Thoughts
It may sound like a cop-out but a panacea is a long way off. The pandemic has certainly been a driver for innovation in the technology space but it cuts both ways, it has also created a smarter criminal.
It is a multi-layered problem and it will be up to organisations to decide on their acceptable level of risk and what an appropriate identity proofing method looks like for their own user community. Perhaps a complete paradigm shift is required to wrest away the the guardianship of identity from agencies and onto the individual but that will more than likely introduce its own set of problems, such as what would happen if the individual forgets the one "key" that unlocks their identity.
What is clear is that there will have to be a combination of culture change, technologies and techniques in order to keep our identities secure.
