
IBM and the Zero Trust Architecture
24 June, 2021, by Stephen Swann
The National Institute of Standards and Technology (NIST) have defined the term Zero Trust (ZT) as an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. At its heart, Zero Trust means there is no implicit trust granted to anything based on network location or asset ownership. In effect Trust Nothing, Verify Everything becomes the mantra.
Authentication and Authorisation of both the user and the device should be performed prior to granting access to any resource. More importantly, that resource should be something discrete rather than something generic like an application or a network segment. The mere implementation of a firewall, or the establishment of a verified session is no longer enough to establish trust. Each interaction should be re-verified!
The architecture as defined by NIST is made up of components that perform functions such as:
- User authentication and authorisation
- Device authentication and authorisation
- Identity governance & management
- Certificate management
- Threat Intelligence
- Logging & monitoring
- Security Information & Event Management (SIEM)
- Data access policies and enforcement (DLP)
- Incident response (SOAR)
One of the few vendors who can provide solutions to each of these architectural components is IBM. The following image shows the NIST architecture overlayed with the IBM products (in blue circles) that satisfy the component requirement:
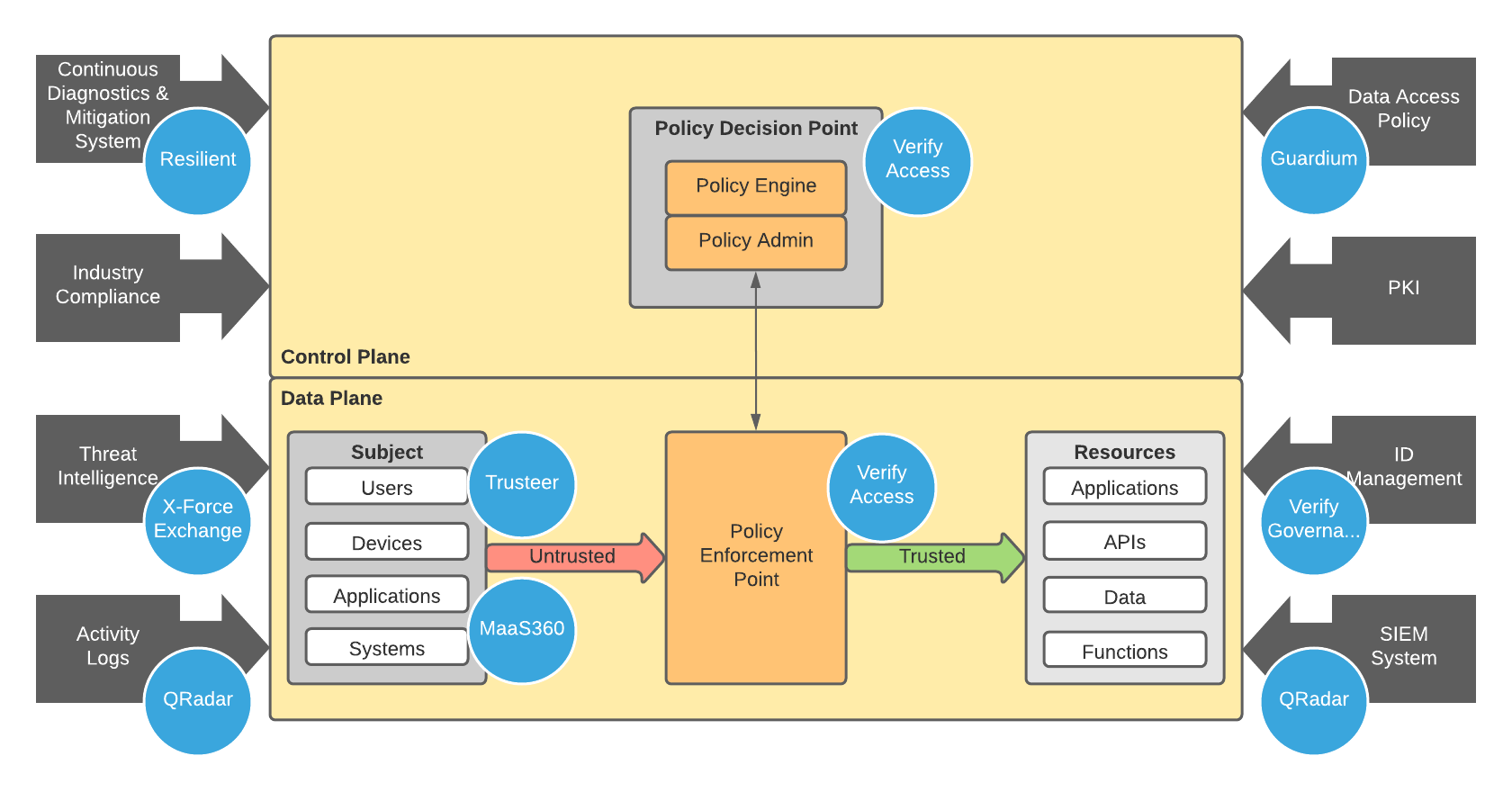
That's a good number of blue circles covering all the major technical components of the Zero Trust architecture. More importantly, each of those blue circles represents a best-in-class piece of technology. The take-away message from this image is that there is a single vendor out there who can satisfy the demands of the Zero Trust architecture. These days, organisations want to simplify the vendor relationships they have and being able to engage with a single provider of a range of security solutions and services is seen as a key differentiator.
IBM & Madigan Solutions
At Madigan Solutions, we want to help organisations achieve Zero Trust. Our expertise lies with the IBM Security Verify suite of products which encompasses:
- Verify Saas: A SaaS solution for policy administration & enforcement and governance
- Verify Access: On-Premise/Hybrid Policy administration & enforcement
- Verify Governance: Identity Governance & Management
- Verify Privilege: Privileged Access Management
The IBM Security Verify suite is at the core of the Zero Trust architecture in that it focuses on users, assets, and resources. The suite can ensure that users are only assigned the privileges they are entitled to; enforce strong (and adaptive) authentication; and continually perform authorisation checks based on user, device and the resource being accessed.
We can help integrate these products with other IBM Security solutions and we partner with specialists in Security Information & Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR) & Data Loss Prevention (DLP), as required.
Contact Us to learn more about how the IBM Security Verify suite can help you on your journey towards Zero Trust.
