
Notes from the Field: PAM Pipelines
24 July, 2023, by Síofra Murtagh
Event Pipeline Policies are a way to trigger actions in response to events that occur within IBM Security Verify Privilege Vault (aka Secret Server). Example events and action responses could be:
- Secret Changed: notify owner via email
- Heartbeat Failed: reset secret password, post a message to Slack, re-run the heartbeat
- User Login Failure: run a PowerShell script, sent an email to the administrative group highlighting the user's incompetence
There are 45 triggers associated with secrets, and 18 triggers associated with users. That's a lot of triggers to play with!
An Event Pipeline Policy can be made up of one or more pipelines that run in sequence with the policy and associated pipelines being associated with a event target type, for example, secrets, folders or users.
NOTE: An Event Pipeline can be associated with many Event Pipeline Policies. As such, updating a pipeline may impact on multiple policies!
Creating an Event Pipeline Policy
Navigate to Admin > Event Pipeline Policy. Select Add a Policy.
You will be given the choice of three actions:
- Create a new policy
- Import a policy
- Duplicate a policy
When creating a new policy, you will be prompted to input a name and provide a description.
Creating an Event Pipeline
Navigate to Admin > Event Pipeline Policy. Select Pipelines from the submenu list, then select Add a Pipeline.
A prompt for the pipeline target type will be presented. Select either Secret or User, then select Create.
A wizard set up guide will appear and prompt you for the following:
- Trigger selection: to detail the trigger event for the pipeline
- Filter selection: to allow for finer grained selection of triggers
- Task(s) definition: to detail the actions to be undertaken
To add a task, select from the comprehensive list of supported actions, then provide the details required for that task.
The following example details the the information required for posting messages to Slack via a WebHook:
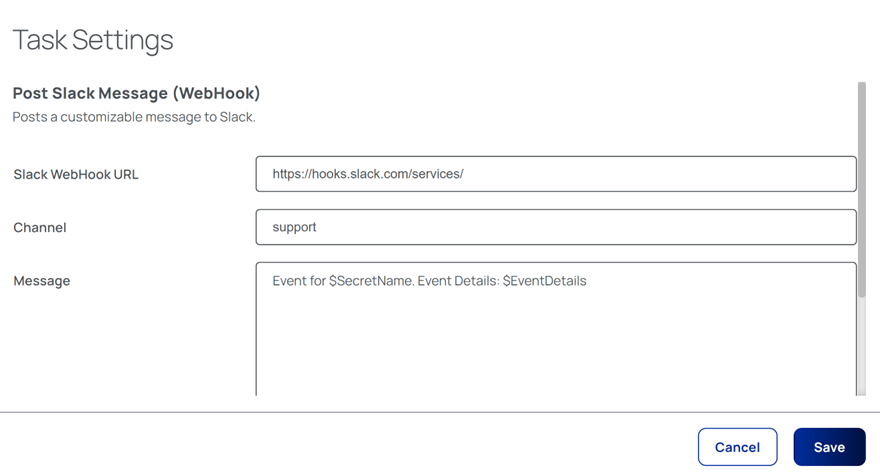
It is important to remember that all tasks are dependent on the successful completion of the preceding task. In effect, a failure of any task will result in the immediate termination of the entire pipeline!
Once a pipeline has been created, it can be activated/de-activated as necessary.
Infinite Loops - A Gotcha
Sometime this can happen when Event Pipelines trigger each other. For example, This can be set off by editing a secret which causes a trigger to the heartbeat the heartbeat then might trigger a different Event Pipeline to edit the secret this will loop on to back to triggering the heartbeat again and can create a feedback loop.
Secret Server is clever enough to detect infinite loops and will deactivate the offending Event Pipelines automatically.
Event Pipeline Monitoring
The effectiveness (or otherwise) of an Event Pipeline can be validated and reported upon. Both the configuration history and the activity history of a pipeline can be viewed by navigating to Event Pipeline Policy > Policies > {Policy} and selecting either the Details or Activity tabs.
