
Notes from the Field: PAM Proxies
12 July, 2023, by Síofra Murtagh
What Is A Proxy
By default, the launching of a privileged session with the IBM Security Verify Privilege Vault tool will create a direct connection from the client machine to the target server - whether that connection is via RDP or SSH.
But oftentimes, there won't be a network route between the client and the server. Indeed, it may not be desirable from a security perspective to even allow such a direct connection.
Allowing users to have unmonitored and unregulated access to communicate with other computers on the network creates a security risk. Whether intentional or otherwise, user actions could put the entire network at risk by compromising a machine. But restricting access so that end user computing devices cannot establish a session with target servers can be achieved by enabling the proxies.
By setting firewalls and updating group policies on an individual host basis, you can ensure sessions are locked down to allow access coming from the Secret Server host only.
To improve the security of your environment, enforcing access via proxies would seem like a no-brainer. But there is an added security benefit with the proxy deployment! The commands that can be issued within the proxy can be restricted too. Just watch a malicious actor attempt an rm -Rf * within a secured proxy server!
The Set Up
Enabling a proxy with Privilege Vault requires no software installation as the proxy capability is built into the product. All you need to do is click a few buttons, update your firewall and/or group policies and away you go.
All RDP and SSH connections can be routed via either the Privilege Vault host or the Distributed Engines. This restricts access to only those confirmed Privilege Vault assets and provides for a highly available architecture.
To enable the proxying configuration, you merely have to follow these steps:
Step 1: Admin > Proxying > Enable SSH proxying
This generates a key (store this key in a secure location)
Step 2: Enable proxying on web nodes, select the endpoints tab and set the public host IP address and Bind IP Address (unique to the proxy).
NOTE: To enable proxying for specific sites and engines within them, set the appropriate SSH proxying port against the approprite site/engine.
Proxying can be enforced for individual secrets by selecting the secret and selecting:
General > Other Security > Edit > Enable Proxy
When proxying is enabled for a secret, the launch sequence will iterate through the engines available for a site looking for an available proxy server or use the Privilege Vault host server as the proxy.
Command Restriction
Privilege Vault supports the creation of command menus which can enforce command restrictions on end users. To do so, select:
Admin > SSH Command Restrictions > Create Allowed Command Menu
Add the permitted commands as required and then save:
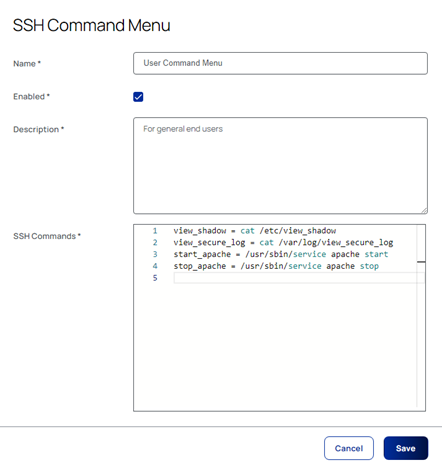
Rather than provide a list of commands that can be issued, however, it is also possible to provide a list of commands that they cannot issue. To do so, select:
Admin > SSH Command Restrictions > Blocked Command lists > Create Blocked Command List
Select commands to add to the blocked list from the list provided (or create your own restricted command list):
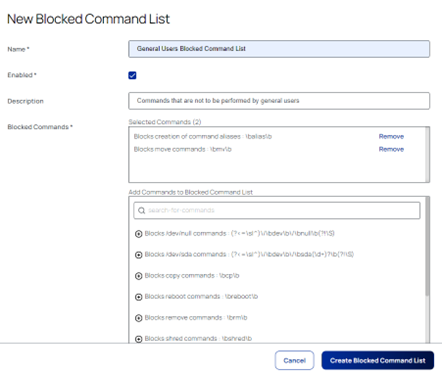
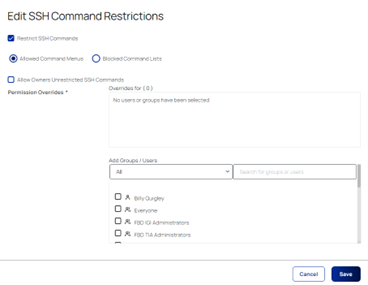
Once the set of allowed/restricted commands have been set up, they can be applied to individual secrets as necessary. To do so, select the secret that you wish to update, and select:
Allow/Block list applied > Security > enable Restrict SSH Commands
Follow the instructions on-screen to apply either allowed or restricted lists, as necessary:
Summary
- Users must log into Secret server and complete 2FA to confirm identities before gaining access to privileged secrets
- Sessions are recorded and store for auditing purposes and can be viewed at any time by the PAM administrator
- Key strokes are recorded with advanced session recording
- By having all sessions launched through secret server via a proxy, users do not have direct access to the credentials that are being used to launch sessions and passwords are managed by Secret Server and rotated on a regular basis to increase security
- If credentials are compromised the hacker will be unable to take advantage and corrupt the hosts as they will be locked out because all traffic must come directly from secret server to gain access to a session
To arrange a free PAM Maturity Assessment workshop or to see a demonstration of Privilege Vault, click here.
