
Risky Business: Cybersecurity response to Covid-19 – time for a review?
06 July, 2022, by Natasha Free
If you are one of the many businesses in the UK who had to rush through changes to accommodate work from home systems during the pandemic, is it time you took a step back and an honest look at what you could have done better?
The sheer scale of digital transformation undertaken has increased the risk of data breaches or issues with business-critical systems. According to the UK government Cyber Security Breaches Survey 2022, 39% of businesses have reported a cybersecurity breach or attack in the last twelve months.
Soberingly, a recent report from McKinsey flagged that “cybercriminals recognize that the data security measures currently in place are ‘not fit for purpose’ or sufficiently robust to prevent them from making successful cyberattacks.”
Seemingly, cybersecurity was not always a key priority in the fast deployment of remote working capabilities!
So where should you focus your attention when reviewing the technical sticky-plasters that have been applied over the last 2 years? There are three key areas worth focusing on:
Remote Access
Is your VPN solution up to it? It is likely that this is not a long-term option you want to stick with anyway since they are notoriously difficult to scale and are an administrative pain.
There is a possibility that the associated certificates are not encrypted and there is always the temptation to issue only one cert for all users.
A VPN for business is yesterday’s (nay last century’s) access management tool. Look for something modern, scalable and with fine-grained access control that can also deal with legacy on-premises applications. No more certs and maybe (one day), no more passwords.
BYOD
Take stock of whether any users are still working with their own devices.
Shadow IT can be a major security risk and enterprise detection and prevention measures are not as sophisticated at home. There are some quick and effective endpoint management tools out there but if users must BYOD, then ensure that they are using up to date Anti-Virus software and undertaking malware scans.
It also seems obvious but not everyone has their equipment set to automatically install software updates. It’s also quick and effective to ensure that users devices are set with PINs and timeouts.
Password protection
Passwords alone provide insufficient protection and are all too easy to compromise. Users are easy prey for ‘credential stuffing’ because so many of us are still using the same username/password combination across multiple accounts.
Consider (at the very least) introducing Multi-Factor Authentication – a step that should be trivial if you issue staff with mobile devices. If possible, go completely passwordless! And remember, password vaults are not just for privileged accounts! Consider making everyone use a password vault as it will encourage the use of assigning different (and stronger) passwords for accounts.
The Road To Maturity
There are many tools out there that are simple to deploy and can address your core access management requirements effectively. You don’t have to use all the functionality at once because they ought to scale in line with your journey to IAM maturity.
For smaller organisations, access management tools may be simpler to implement and are certainly cheaper than all singing/all dancing SIEM tools most of which have been designed for enterprise scale organisations anyway. In my opinion, proactive security is always better than reactive!
If your organisation is ready for the next step, you can look at vulnerability management, data access/leakage policies, threat intelligence, and proper layered security within a Zero Trust framework.
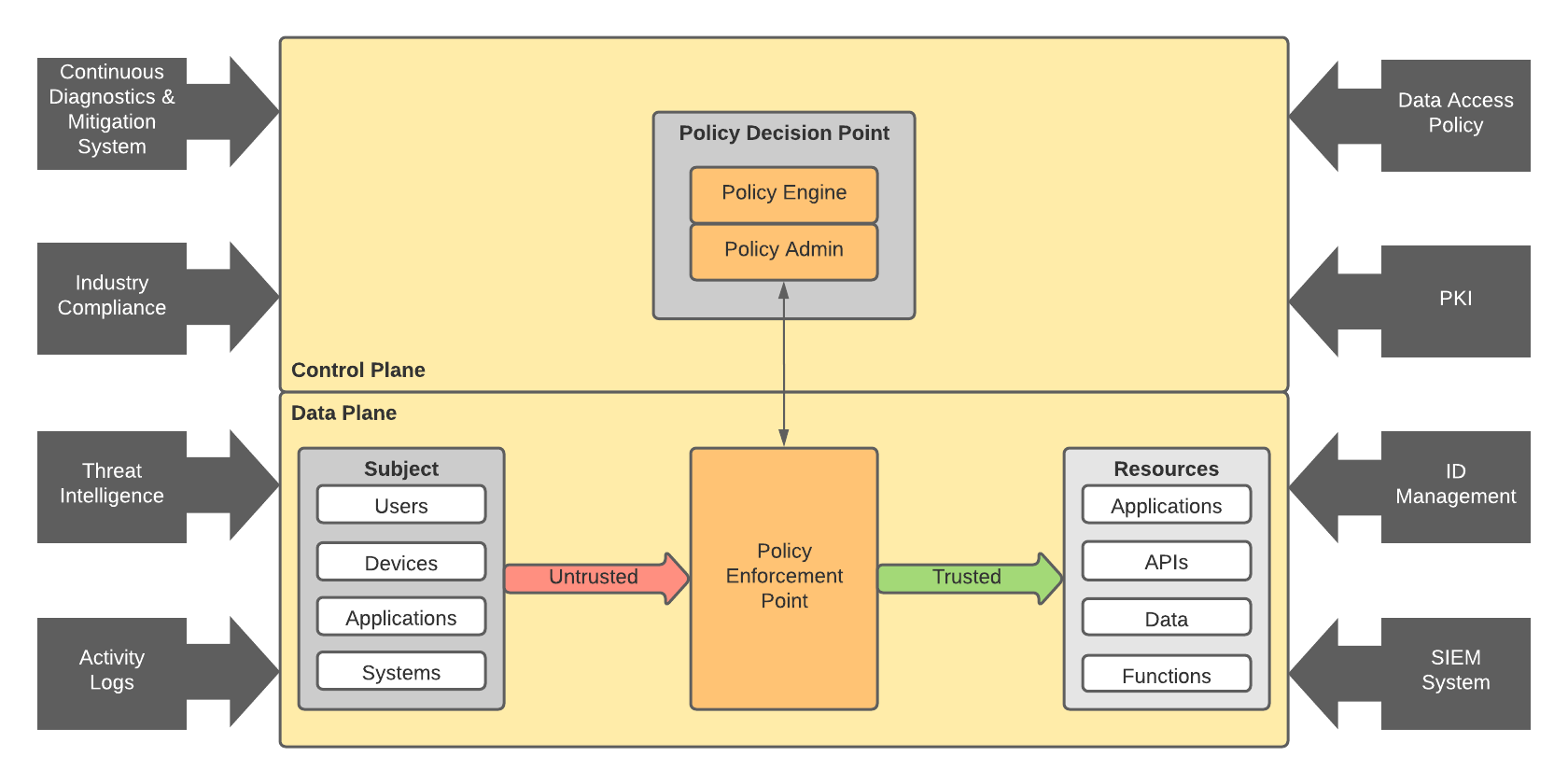
And don’t forget to address the human side - educate and focus on what people CAN do, rather than what they SHOULD NOT be doing. A few simple changes can get you back feeling more confident about your security posture.
References
- UK Government Department for Digital, Culture, Media & Sport: Cyber Security Breaches Survey 2022
- McKinsey (Boehm et al) March 2020: Cybersecurity tactics for the coronavirus pandemic
