
Zero Trust Through Identity & Access Management Best Practice
14 July, 2021, by Natasha Free
Zero Trust shifts the focus away from the concept of a secure perimeter to focus on a virtual perimeter around all users, assets, and resources. The principle of Zero Trust could be distilled into one easy to remember mantra for access: Never Trust, Always Verify!
The National Institute of Standards and Technology have defined what they believe a Zero Trust Architecture looks like and it is striking how critical Identity & Access Management concepts are within the architecture.
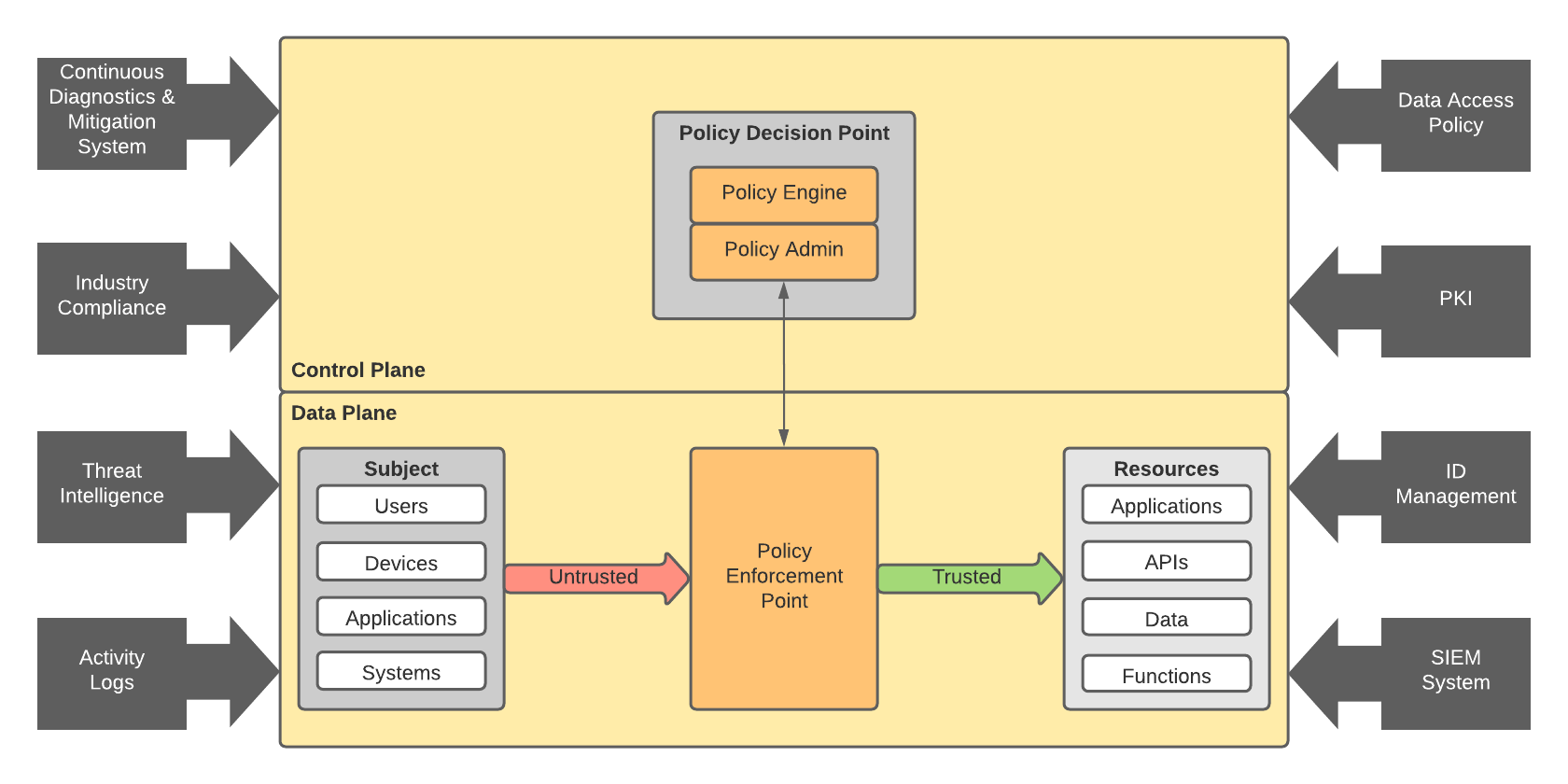
So, as more organisations look to secure their increasingly disparate applications, users, and data we wondered where one might start on the Zero Trust journey. Here are 5 things you can do to help you on your way.
Risk Analysis
Taking a risk-based approach will help you to focus on your high-risk vulnerabilities and critical assets & services:
- Do you have a high user churn?
- Do you regularly make large transactions?
- Do you have a high number of work-at-home users still logging on with their own devices?
The output of this analysis should be robust and well thought out policies that fit your business needs. But we all know that policies cannot be static and a good approach to security will change with the times and threats. It is therefore helpful to have somewhere where you can centrally and easily adapt those policies to support the ever-changing use cases and requirements.
Authentication and POLP
A Zero Trust approach to user access should always start with the Principle of Least Privilege (POLP). Enforcement of Least Privilege ensures access to key business systems is limited to only those requiring access at that time. It can also help you proactively ensure that when credentials are abused, privileges are limited.
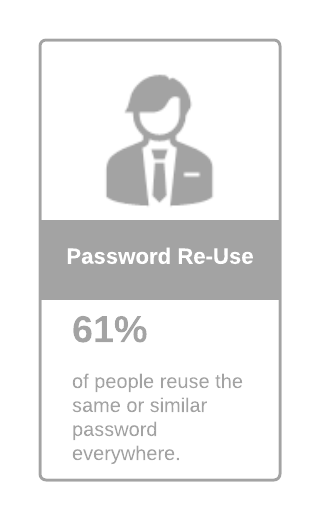


Authenticating users is your first line of defence but do not trust passwords! 61% of users reuse their password everywhere so they cannot be trusted. A better way to establish trust is to ensure that the user has provided a second factor of authentication. There are a number of ways to implement multi factor authentication (MFA) so you should be able to find one that suits your user community and the technology they have at their disposal. If you have concerns regarding the user experience, then consider integrating the MFA journey into an adaptive and context-based authentication flow. For example, enforce MFA when the user's device or network has changed.
Take control down to each application, server or API. This ensures that every user, every device, every connection must prove a legitimate need before access is granted.
Privileged Access Management
What happens where trust is most critical and most vulnerable to exploitation? Administrative access and shared accounts can be a real headache. Clear privileged access policies with active monitoring and time boxing of user access are essential.
Modernisation
Stay ahead of the curve and update access protocols. OAuth and OpenID Connect provide assurance that security best practices are followed.
Device fingerprinting may provide insight for the risks surrounding BYOD (currently working from home!), and feed into your Zero Trust authentication protocols.
Governance
Good governance and enforcement will go a long way to instilling a Zero Trust ethos.
Auditing is generally dull but can be less of a drag with good monitoring and reporting in place. If you have implemented continuous authorisation checks on the user, device and the resource being accessed, then you will want to be able to validate that those controls are working. This will not only help to consolidate the work you have put in, but also identify any areas in need of improvement.
Even something as simple as enforcing password security best practices can significantly reduce risk. And don’t forget the auditors! Can you demonstrate compliance and continuous improvement?
Continuous recertification of the entitlements assigned to users isn't just a "good idea", it's a critical tool in ensuring that users are only assigned the privileges they are entitled to. The auditor will be happy to see the results too!
