Identity Threat Detection & Response
Identity is now widely recognised as the number one attack vector. According to the 2024 IBM X-Force Threat Intelligence Index, 60% of all attacks in the preceding year focused on weaknesses in IAM. Are you confident you can quickly detect identity threats across your network and applications?
Learn More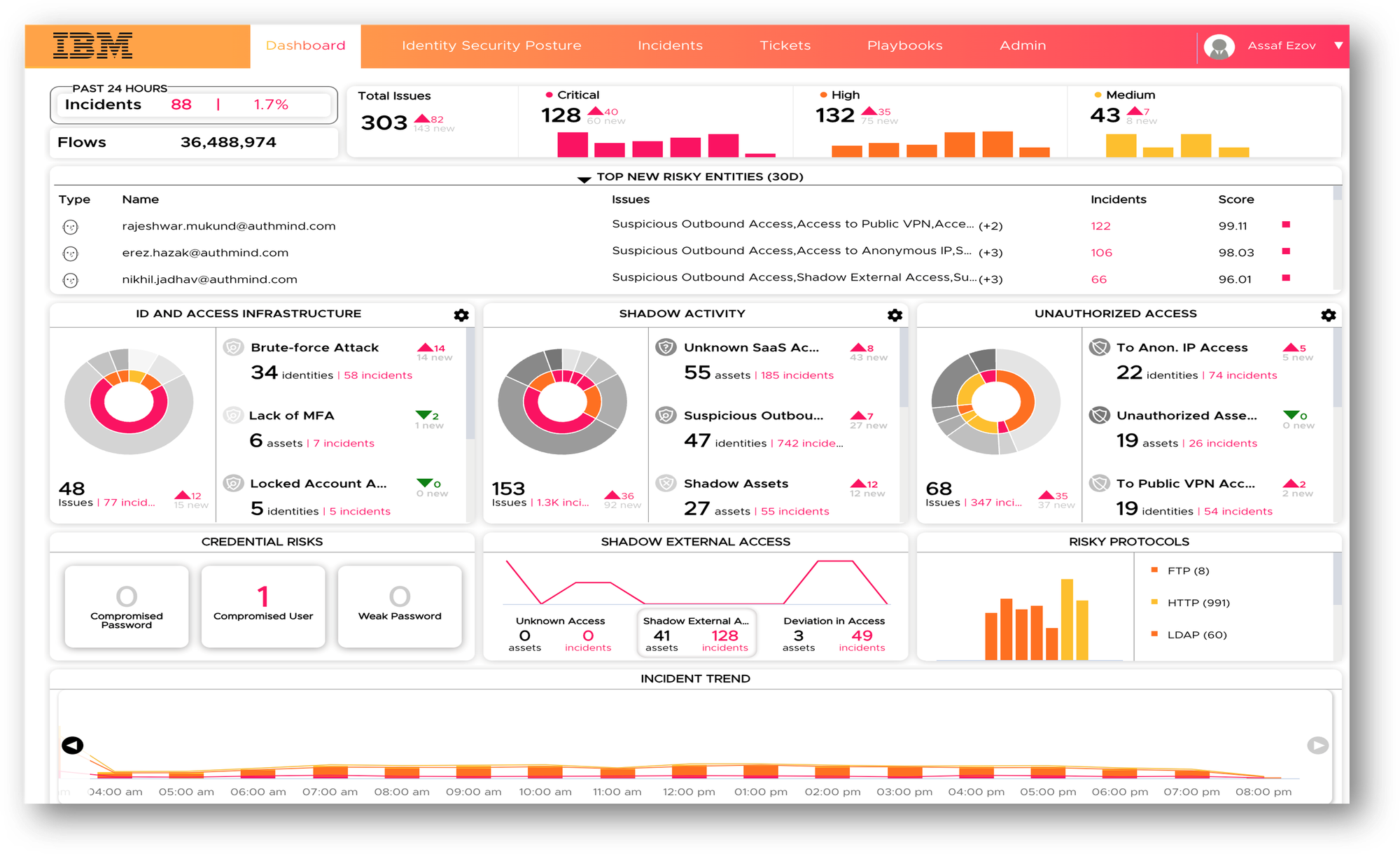
IBM Verify Identity Protection

Verify Identity Protection
Who is attacking the organization?
Which assets are they accessing?
Where are they accessing them from?
How are they accessing them?
Identity Infrastructure Issues
- MFA issues (e.g., bypass)
- Credential hygiene
- Service account security
- Suspected attacks on identity systems
- Dormant system detection
Identity Blind Spots
- Exposed assets
- Shadow assets
- Shadow identity systems (e.g., directories)
- Shadow password managers
- Shadow SaaS usage
Risky Identity Activity
- Bypass of ZTNA
- Bypass of VPN
- Bypass of MFA
- Suspicious access/identity activity