Identity Governance & Administration
The scale of systems connectedness and the expansion of Cloud computing has forced application providers to re-think their approach to cyber-security. The increase in potential risks to business and service mean that we have entered the age of Zero Trust: Trust Nothing - Verify Everything.
Learn MoreAchieving Zero Trust, however, cannot be achieved using a single product. Instead, a suite of tools is required to provide the defences that businesses need.
IBM Verify Identity Governance (VIG) helps address the core requirements of an identity governance platform in the context of Zero Trust by providing:
- Automated Joiner/Mover/Leaver (JML) process
- Industry vertical appropriate Risk Analysis engine
- Suite of Re-Certification campaigns
- Wide range of appropriate audit reports




Joiner/Mover/Leaver
The fact that 49% of IT Professionals retain access to their ex-employer's network is a startling statistic. Organisations who already believe they have control over their user community struggle to effectively disable access in a timely manner. However, it is not difficult to resolve this issue.
Verify Identity Governance has integral rules to ensure that users' entitlements and access is assigned and removed at the right time.
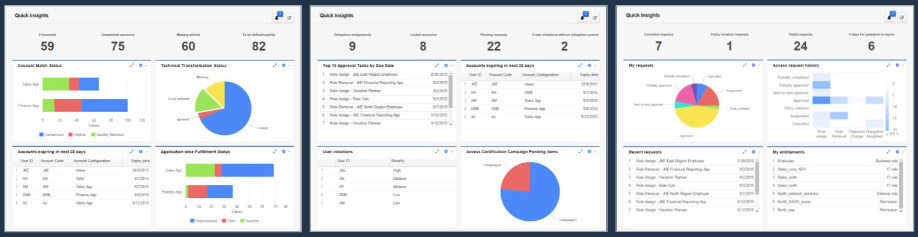
Analytics
Verify Identity Governance brings a wealth of analytical reports and dashboards to a variety of user communities. It provides the right information to the right people at the right time to allow them to make informative decisions.
Learn MoreVerify Identity Governance adds a wealth of reports and data extracts that are appropriate for your business such as:
- Risk scoring and mitigating controls
- Orphan account analysis and remediation
- Role discovery and mining
- Entitlement assignments that deviate from peers' assignments
- Entitlements that were approved by someone who is no longer with the company
- Headcounts per organisation/division/department
Instead of highlighting toxic combination of roles or the assignment of risky permissions, the platform can take your identity analytics to a new level by by seeking out outliers across your enterprise systems and triggering the automatic remediation or re-certification of such entitlement assignments.
Re-certification Campaigns
4 out of 5 users have unnecessary access (according to a recent study by a popular retailer). Verifying that proper access has been assigned on a periodic basis should address that issue right?
Learn MoreConsider this question: Does Jane Jones still require access to the entitlement Abc2178253971051 on the SAP-ERG-PRD system? Who knows? Maybe not even Jane herself!
Instead we could ask: Does Jane still need access to the Open Sales Opportunities capability on the CRM system? And there is a chance that both Jane and her Department Manager might be able to answer that question.
With Verify Identity Governance we have a business-centric approach to asking the questions that ensure that the entitlements assigned to end users accurately reflect their expected business activities.
No more guessing. No more assumptions. No more unnecessary access rights assigned.
Furthermore, wouldn’t it be great if Jane's access to the Open Sales Opportunities capability on the CRM system could be re-certified by the swipe of a finger?
Friction-free approvals embedded into the enterprise communication tool of choice is no longer a pipedream. With Verify Identity Governance you can easily action approval requests from within Microsoft Teams or Slack, making for a better end-user experience whether you’re Jane or Jane’s manager.