Blog Articles

Upgrade Paths Explained
By Stephen Swann
4 years ago
•
2 min read
Tags
• Access Management
• Identity

Is It Time You Upgraded Your Access Management Solution?
By Natasha Free
4 years ago
•
3 min read
Tags
• Access Management
• Modernisation
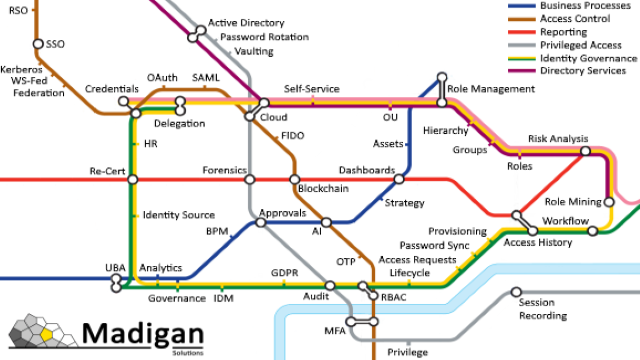
How To Plan Your Identity Journey
By Stephen Swann
4 years ago
•
2 min read
Tags
• Identity
• Access Management
• Governance
• PAM

Could An MSSP Be The Future For Your IAM Needs
By Paul Kennedy
4 years ago
•
5 min read
Tags
• MSSP
• General Security

Free Talking - Episode 4
By Natasha Free
5 years ago
•
2 min read
Tags
• Free Talking
• General Security
• Podcast

Free Talking - Episode 3
By Natasha Free
5 years ago
•
2 min read
Tags
• Podcast
• General Security
• Free Talking

How To Control Non-Human Identities
By Stephen Swann
5 years ago
•
3 min read
Tags
• Governance
• Zero Trust
• IOT
• UMT
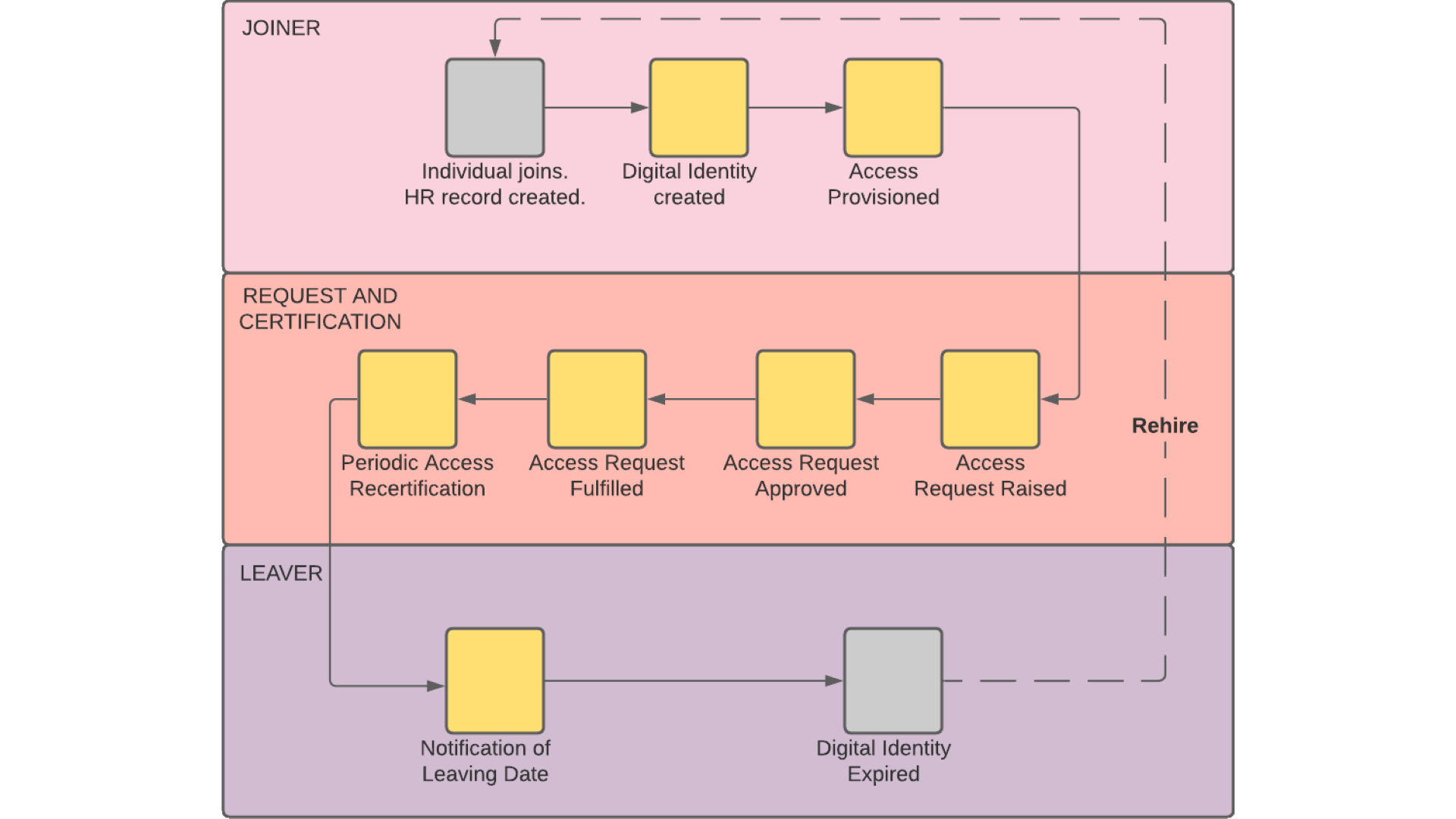
Simplify Your User Lifecycle Management
By Simon Young
5 years ago
•
3 min read
Tags
• Governance
• Lifecycle Management
• Recertification
• SVG
• UMT

Zero Trust Through Identity & Access Management Best Practice
By Natasha Free
5 years ago
•
3 min read
Tags
• Zero Trust